
Penetration Testing Vendors
Is Your Organization’s Security Compliance at Risk?
Ensure compliance with penetration testing and security audits. Talk to our experts to detect vulnerabilities and prevent breaches before they happen.



.webp)




.svg)
.svg)




.webp)




.svg)
.svg)



Our Services
Designed to safeguard your business with precision, speed, and reliability.
Network Pentesting
Expose network security risks through simulated cyberattacks, preventing breaches and unauthorized access.
Web App Pentesting
Uncover SQL injection, XSS, and authentication flaws to strengthen web application security, and protection against data breaches.
.avif)
API Pentesting
Protect REST, SOAP, and GraphQL APIs from injection attacks, misconfigurations, and data leaks.
.avif)
Network Vulnerability Assessment
Identify security vulnerabilities in web applications, prevent data breaches, and enhance website security.
.avif)
Web Vulnerability Assessment
Identify security vulnerabilities in web applications, prevent data breaches, and enhance website security.
.avif)
Compliance Bundle
Ensure security compliance by identifying risks in web apps, servers, APIs, and databases to meet GDPR, ISO 27001, and industry standards.

Stay always ahead of hackers

“When we identify vulnerabilities, it’s remarkable how much valuable information they provide. The recommendations are clear and highly useful.”
Let our experts evaluate what your organization needs to make it secure for your clients.

Choose Alphabin as your trusted pentest partner
Your security matters. Our expert-led, real-world testing approach ensures reliable protection against cyber threats.
Deep Pentesting
Worried about undetected vulnerabilities? We conduct in-depth, manual testing to uncover security gaps that automated tools miss.
Hacker Like Testing
Think like an attacker, defend like a pro. Our ethical hackers simulate real-world cyberattacks to expose your system’s weak points.
Comprehensive Report
Confused by security jargon? We provide clear, actionable reports with risk ratings and step-by-step fixes for every issue
Process Based Testing
Need compliance-ready security? Our structured testing follows OWASP, NIST, and PTES standards to ensure reliable results
Help in Vulnerability Fixing
Finding issues is just the start. We guide your team with hands-on remediation support to fix vulnerabilities quickly.
Impressive Track Record
Proven results, trusted by businesses. With successful pentests across industries, we help organizations prevent real-world attacks.
.svg)
How Our Penetration Testing Process Works
Planning & Risk Assessment
Define intruder models (internal/external threats, privilege escalation).
Determine testing scope, target systems, and security goals.
Develop a customized penetration testing strategy for your business.

Attack Simulation & Vulnerability Exploitation
Define intruder models (internal/external threats, privilege escalation).
Determine testing scope, target systems, and security goals.
Develop a customized penetration testing strategy for your business.
Reporting & Security Enhancement
Provide a detailed penetration testing report with risk prioritization.
Offer step-by-step remediation strategies for security improvement.
Conduct free retesting to validate fixes and ensure compliance.
.avif)

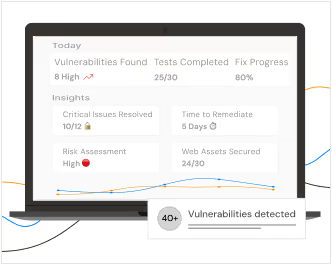
Actionable Reports for Instant Risk Mitigation
Our reports provide a clear, actionable, and comprehensive insight into your security posture—going beyond just well-structured documents.
Actionable Insights, Not Just Data
Get testing reports with clear risk prioritization and remediation steps, so you know what to fix first.
Compliance & Audit-Ready Reports
Ensure regulatory compliance with structured reports designed for auditors, executives, and security teams.
.avif)
.svg)
Continuous Compliance with Penetration Testing
Stay compliant with top security standards through ongoing penetration testing and actionable insights.
.svg)



.svg)



- Continuous Security Assessments to maintain compliance
- Automated & Manual Pentesting for risk identification
- Real-Time Compliance Insights to track security gaps
- Regulatory Reports & Audit Support for hassle-free certification

Explore Important Resources
Here are some useful case studies and blogs to help you get started on your security journey.

Frequently Asked Questions
We can typically begin with an initial consultation call within a few business days of your inquiry. During this call, we’ll clarify your objectives, discuss scope, and outline the timeline for the testing phase. Simply fill out the form or request a call-back, and we’ll schedule a time that works best for you.
Our pricing depends on factors like the complexity of your environment, the number of systems or applications to be tested, and any specific compliance requirements. After we learn more about your needs in a brief discovery call, we’ll provide a tailored quote that outlines cost, scope, and timelines.
We conduct our tests with minimal impact on your operations. Before we start, we’ll coordinate with your IT team to define acceptable testing windows and methods. Our experts follow best-practice methodologies to ensure that testing is safe, controlled, and causes little to no downtime.
You’ll receive a comprehensive report detailing all findings, including vulnerabilities discovered, their severity, and recommended remediation steps. If you have industry-specific compliance needs (like PCI-DSS, HIPAA, or GDPR), we’ll ensure your report includes evidence and recommendations aligned with those standards.
Alphabin offers post-engagement services to help you address and remediate any vulnerabilities identified. We can assist with patching, configuration changes, and even re-testing to validate that all issues have been resolved. Just let us know, and we’ll tailor an ongoing support plan to keep your systems secure.
.svg)
Automate your regression 5x faster with AI
See How in a Quick 15-Min Demo


.svg)
.svg)
.svg)
.svg)
.svg)
.svg)
.svg)



